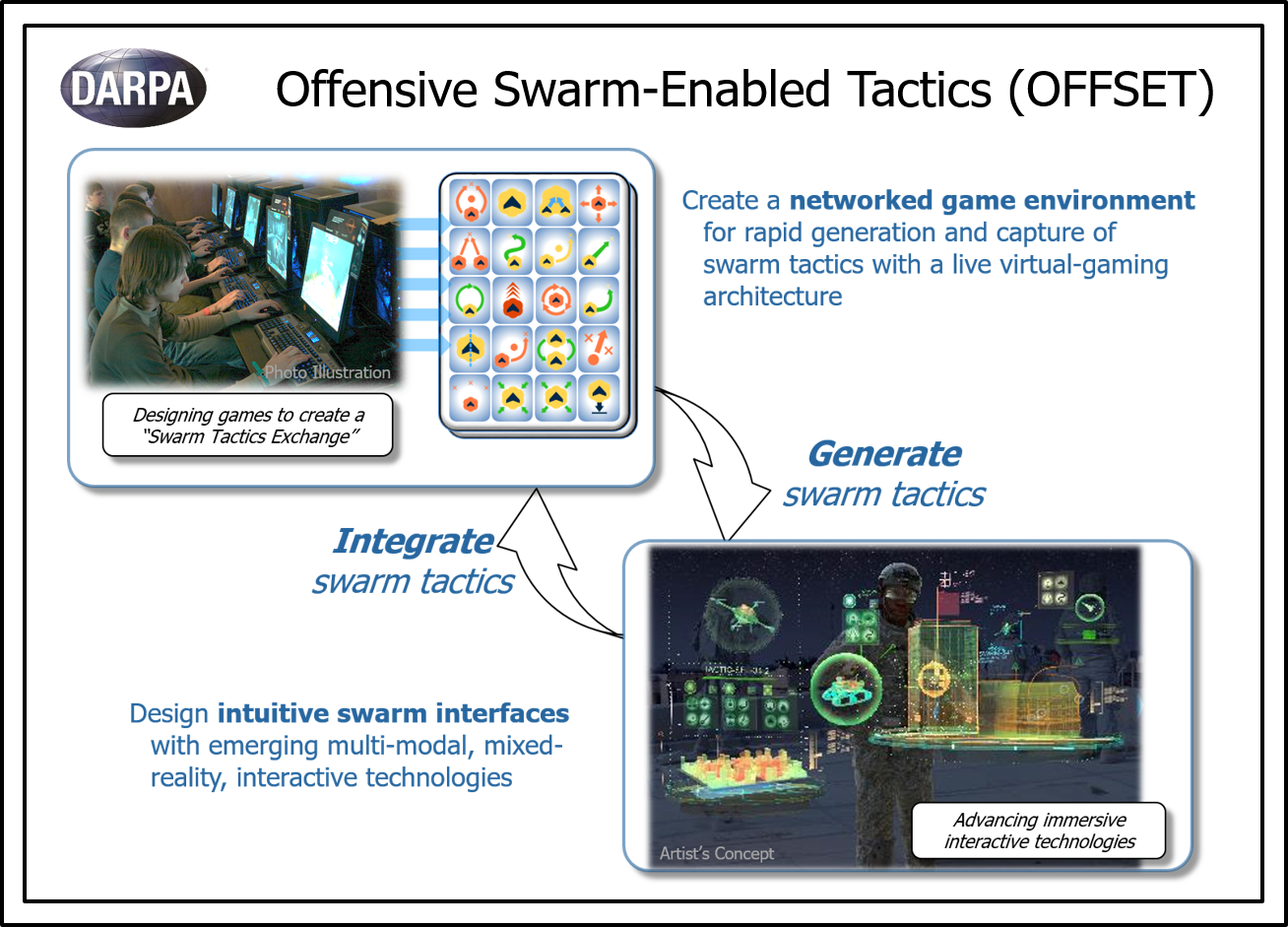


Three keys to standing up the Army’s Modernization Command [Commentary]
As the Army stands up the Modernization Command, it faces some daunting, yet addressable challenges. Here are the big obstacles they need to overcome.

Net Defense Blogs
Solving the challenges of change [Commentary]
Change is not easy and what the Army has been undertaking with its network strategy can best be described as a paradigm shift. However, wideband technology is a game changer and we should sprint forward to put this capability in the hands of the war fighter. So how and why aren’t we closer to success?

The FY18 Defense Authorization and insider threat [Commentary]
As the fiscal 2018 NDAA winds its way through Congress, it is worth noting how differently the House and Senate are treating matters related to reducing threats from insiders.

Is machine learning the answer to the data deluge?
With the right investments, intelligence analysts can be empowered to effectively analyze and integrate ISR data as it comes in.

The challenge of digitization and technological advancement
Familiarization with technology promotes a level of comfort that is difficult to achieve with those that did not grow up with the internet.

Getting — and staying — one step ahead
Are existing policies and regulations impeding our military’s and intelligence community’s ability to respond and react in a near-real time manner that is a fundamental requirement today?

A ‘cyberwar’ definition remains problematic
There are many complicated questions posed while defining the cyberwar battlefront.

The case for the software-defined battlefield
After more than 15 years of nearly constant deployments, the U.S. military’s balancing act between modernization and readiness is reaching a tipping point.
The issue of singularity
Multiple technologies are emerging that individually will change multiple aspects of military operations. That is one of the areas where the issue of singularity becomes much more acute.

The business of national cybersecurity
With all the attention over cyberthreats, one would think the business of national cybersecurity would be very robust. Well, that depends who you talk to.

Cyber training and education must be continuous [Commentary]
Considering the pace with which technology is advancing and implemented, it is easy to see just how essential continuing educations has become.
The weird science of quantum computing, communications and encryption
Quantum theory is the abstract basis of modern physics. It explains the nature and behavior of how matter acts.

Cryptocurrencies — a growing issue for military, intel agencies and law enforcement
While many have not heard of or understand cryptocurrencies, you had better take notice — that is for sure! This is a powerful technology whose ramifications mandate that military, intelligence organizations and law enforcement must monitor and understand it.

The weaponization of words and conversations
The connected world in which we live has transformed words and conversations into weapons.

The complexity of developing a cyber defense strategy
For decades, our adversaries have been and continue to constantly seek new ways to compete with the United States on a much more level battlefield. Cyber has much, if not all, of what they have been looking for.

WannaCry: Top 5 lessons learned
The WannaCry ransomware brought with it some unexpected consequences.

Cyber, biological, crypto: Hybrid terrorism at work
The move to May brought with it a terrorist incident that is likely to resemble an increasing percentage of incidents in the coming years.
