The Department of Defense (DoD) and agencies across the US federal government are preparing for 5G connectivity. With the promise of fast speeds, lower latency and stronger authentication mechanisms, 5G powered networks present significant new benefits and exciting possibilities. Agencies’ internal network teams, contractors, or traditional service providers will adopt private 5G subscriptions to run small cells where needed—for example, on a military base, an agency campus, or even a ship. These 5G networks will accelerate exponential growth of connected Internet of Things (IoT) devices, which will be increasingly integrated into defense infrastructure.
As we approach this new frontier, the security of any new 5G network must be factored in from the start. 5G will require at least the same level of protection that we have seen for years across more traditional agency IT networks through practices like implementing a security operations center (SOC), proper asset management, and continuous monitoring. Augmenting these practices with modernized approaches like Zero Trust and automation will enable agencies to harness the power of 5G safely and for the long term.
Applying 5G’s Advanced Features
Multiple new features make 5G a quantum leap forward in capabilities.
Network Slicing
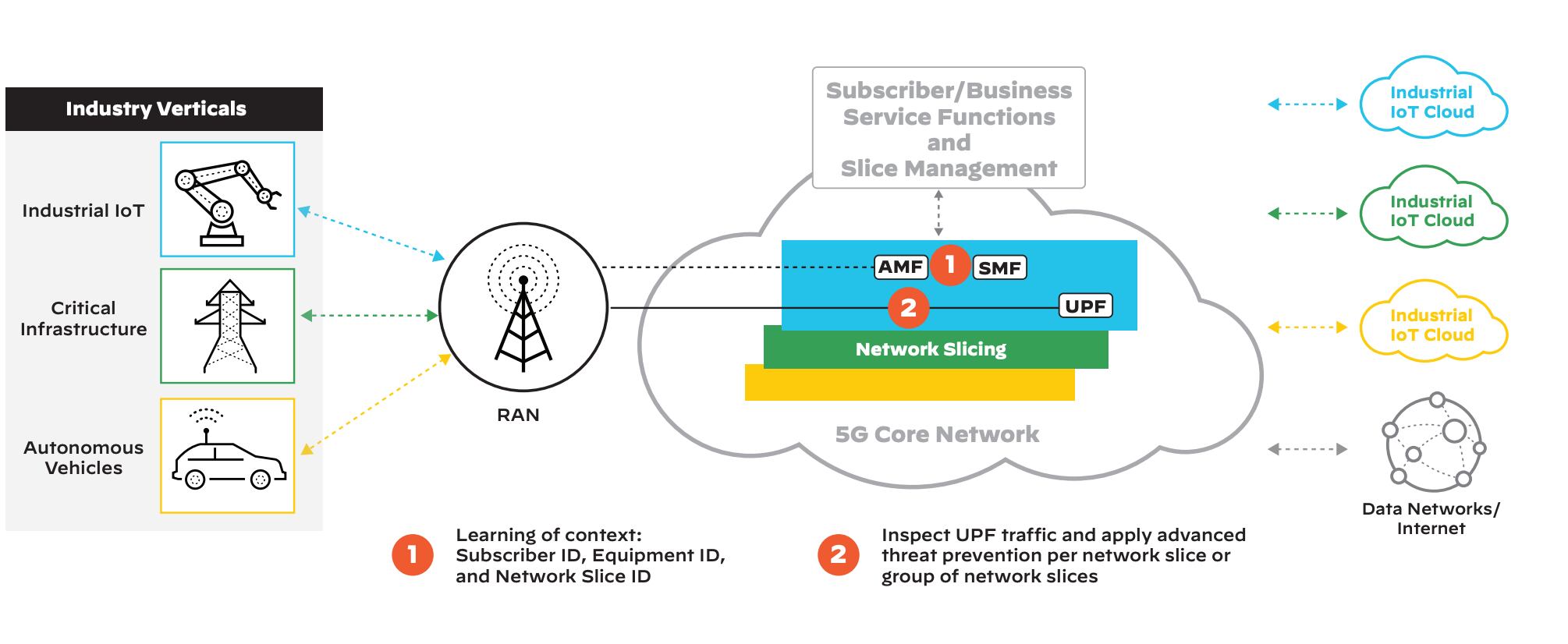
One of 5G’s most powerful new capabilities is network slicing, a way to virtualize the 5G network into segments utilizing software-defined networking (SDN). Network slicing ensures high network performance, reliability, and speed for a breadth of applications and devices. It enables advanced capabilities such as:
• Enhanced Mobile Broadband (eMBB) for high data transfer rates across a wide coverage area
• Ultra-Reliable Low-Latency Communication (URLLC) to support mission-critical applications (e.g., smart grid) that need extremely high speed and reliability
• Massive Internet of Things (MIoT) to support many IoT devices in a small area
Importantly, network slicing will allow network traffic from purpose-built devices (e.g., drones, telehealth devices, weapons systems) to be prioritized over traffic from lower priority devices like mobile phones and laptops.
Wired Replacement
Wired replacement will enable a vastly increased level of continuous connectivity for mobile users and devices moving throughout 5G-enabled environments. By replacing traditional network jacks or more limited wireless networks, 5G cells installed in a building, campus, ship, or aircraft will offer highly flexible and continuous connectivity for users and the growing number of IoT devices. 5G will provide far more net- work throughput and stability beyond current 3G and 4G networks, delivering more reliable performance and connection to applications, the cloud, and the internet.
Multi-Access Edge Computing
Multi-access edge computing (MEC) represents an evolution in distributed computing, accelerating information processing so that sensors and IoT devices will be collecting vast amounts of data in need of fast analysis. Acting as kind of a localized private data center, edge computing utilizes containerized analytics applications running on limited hardware at the edge for real-time analysis. Bypassing the transmission of data to remote or cloud-based environments eliminates latency and enables faster decision-making.
Consider, for example, the potential at a 5G-connected Air Force base. Whenever a plane lands, a manually intensive process is required to inspect its integrity for the next flight and replace any faulty components that, if not in stock at the base, must be ordered from a centralized distribution center. Connecting to the aircraft through 5G will enable automatic safety validation checks upon landing, quickly flagging any issues for the engineering team to remediate. Further, connecting parts replenishment requirements into logistics systems can enable automatic ordering as well as tracking of shipping and delivery information.
Ubiquitous Connectivity
Federal networks can provide access to a wide range of users and classification levels known as multi-domain support. This model is used to impose role-based controls for different types of information accessed through the network (e.g., unclassified, public trust, confidential, secret, and top secret). 5G can enable strict segmentation while ensuring broad and ubiquitous connectivity across all network users’ classification levels, regardless of device type.
To continue our connected Air Force base example, the isolated network connecting the airplane diagnostic system should be able to connect well beyond the aircraft being analyzed, to other Air Force networks (logistics, purchasing, etc.) or even other DoD environments. That broad connectivity requires network segmentation, enabled by 5G’s network slicing capability, to ensure multi-domain use cases are securely supported.
5G’s Escalated Security Demands Parallel Traditional Network Requirements
All known federal use cases and many more to unfold hold great promise, but also a greatly increased level of risk. Today, far more capabilities are being vested in technology than ever, over open radio waves rather than closed networks.
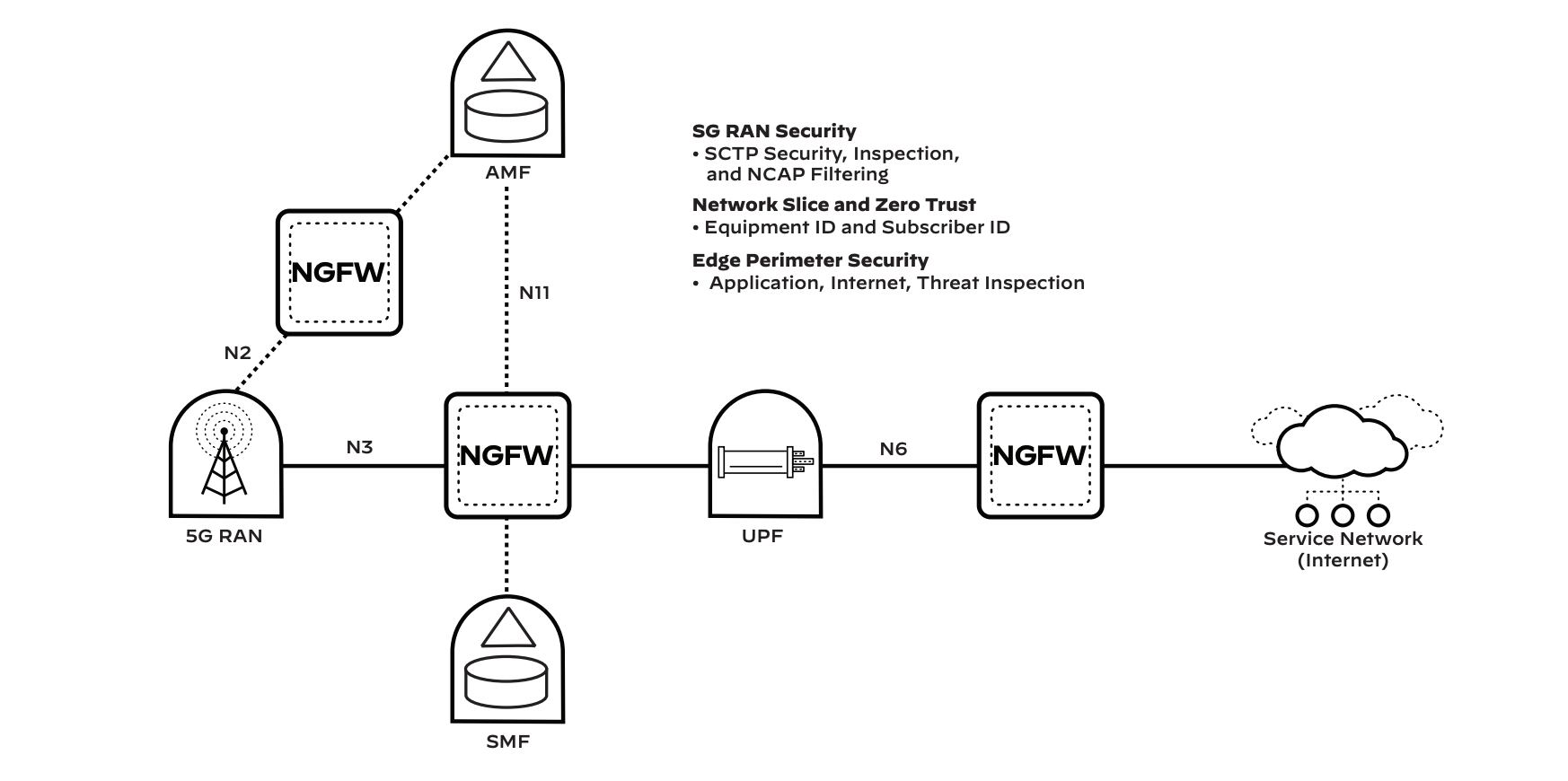
Network attacks frequently target the physical infrastructure of the packet core. Protecting 5G will demand the same level of strict controls and protections as are applied to that physical infrastructure. This requires implementing several proven practices. First is imposing accountability (part of the confidentiality, integrity, and accountability [CIA] triad), enabled through granular logging and deep visibility into encrypted tunnel traffic that is analyzed for threats.
Next is Zero Trust access, an architectural security strategy rooted in the principle, “never trust, always verify.” Segmentation is an important part of Zero Trust, since as with traditional network access controls, 5G users should only have access to what is needed to perform their day-to-day functions. Because new connected devices will rely on analytics from the applications they work with, all network traffic will need to be segmented and prioritized to make sure the highest performance traffic has the necessary quality of service, latency, and network performance.
Also, as with traditional networks, 5G will require determining the subscriber ID, and then applying granular controls to verify how and from where a user or device is attempting to gain network access.
Each type of device will also need to be dynamically protected against known and unknown vulnerabilities. There will be sensors on 5G networks that still use legacy operating systems and vulnerable firmware that must be secured. Exposing those devices to 5G’s power will require deeper visibility and controls, best achieved by automating mechanisms to find device vulnerabilities as well as classify the controls needed to quickly remediate them.
Thorough network protections will be imperative to monitor the critical infrastructure and high-risk devices agencies will be putting into 5G environments. Moreover, as 5G scales to connect more devices, human operators that run legacy SOCs won’t be able to keep up. Automation will be the only option fast and efficient enough to isolate and counter threats as quickly as they’re found.
Palo Alto Networks: First in 5G-Native Security
Palo Alto Networks offers the industry’s first 5G-native security solution, enabling end-to-end security from the control plane to the user plane through the applications. This includes containerized 5G security, real-time correlation of threats to 5G identifiers, and 5G network slice security.
Protecting Devices
Two primary classes of device will connect to 5G.
End User Devices
End users’ mobile devices (e.g., cell phones, laptops, tablets) will not be permanently fixed on the network agencies will lose visibility and control over them at times, creating significant risk. For instance, they will likely travel beyond the boundaries of the private 5G network. They may connect to other open 5G networks or private Wi-Fi, download unsanctioned applications, or even unintentionally install malicious software. Because user behavior cannot be fully controlled, detecting and preventing threats is a requirement for securing 5G infrastructure.
Frequently, after malware is downloaded, it attempts to propagate through the device’s network. Palo Alto Networks provides deeper visibility into the lateral movement of malware traffic traversing a firewall or segmentation gateway, correlating it to the subscriber or hardware identification number of the 5G network user so threats can be isolated and their propagation stopped.
Internet of Things Devices
The other major device class that will connect to 5G is sensor-driven IoT devices. 5G allows for greater networked device density, making it the preferred IoT connectivity fabric. Many IoT devices are already installed on agencies’ networks across a spectrum of functions (even down to connected dish- washers), and many more will follow.
These purpose-built, high-performance devices pose perhaps the biggest security threat to 5G. Typically built on small single-board computers (SBCs), they run lightweight operating systems not designed for security.
To fill the gap, Palo Alto Networks uses network telemetry coupled with machine learning to discover each device on the 5G network and classify it according to its purpose (e.g., camera, medical device, mobile phone). Once a device has been classified, our Next-Generation Firewalls (NGFWs) recommend policies that are dynamically built to allow only normal, acceptable network behaviors of IoT devices in the same device category. Implementing security policies in the packet core allows for more accurate security for IoT devices.
Implementing Zero Trust
Network slicing enables the multiplexing of virtualized and independent logical networks on the same physical network infrastructure. Each network slice is an isolated end-to-end network tailored to fulfill diverse requirements requested by a particular application. Acting as a segmentation gateway, our NGFW implements granular security specific to each network slice, ensuring security, speed, performance, low latency, and delivery for high-priority traffic. Implementing security policies per network slice allows for microsegmentation of 5G traffic. A testament to its quality, our NGFW meets the National Institute of Standards and Technology (NIST) requirements for a policy enforcement point (PEP) specified in Special Publication 800-207.¹
An effective Zero Trust access policy requires defining what specific users or devices can access what resources using what device. Through the combination of Equipment ID and Subscriber ID with our App-ID™, and Content-ID™ technologies, Palo Alto Networks allows for granular Zero Trust policies to be defined.
App-ID inspects the network traffic at Layer 7 to categorize the application. This allows for accuracy beyond just port and protocol when defining application access policies. Equipment ID maps international mobile equipment identity (IMEI) to network traffic, which allows policies to be built for specific types of hardware. This capability also enables agencies to build policies that, for example, only allow Government Furnished Equipment (GFE) on the network or define which applications can be accessed from mobile phones vs. IoT devices.
The last building block of a 5G Zero Trust policy is defining who can access resources. Subscriber ID maps the international mobile subscriber identity (IMSI) to network traffic, enabling access policies to be built around the SIM card assigned to devices or individuals. Combining Subscriber ID with Equipment ID ensures that only authorized users accessing the network with a GFE device can access their needed applications. It also provides segmentation between the user and device network so that only a particular class of device that is assigned a SIM card can access IoT-specific applications.
Protecting Applications
Applications running on 5G networks will be hosted in a combination of the MEC, public clouds, and private clouds. Securing these applications will rely on implementing consistent security, adopting Zero Trust, and enabling DevSecOps.
Centralized visibility and control will be mandatory. Using a single pane of glass for visibility into network traffic, asset security posture, and ongoing network events will give operators a deeper understanding of a 5G deployment’s health. What’s more, using a centralized tool to implement security across the hosting environments will ensure consistent security can be implemented and maintained.
The Palo Alto Networks NGFW can be deployed in physical, virtual, and containerized form factors to meet the flexible needs of the varied hosting environments. Our Panorama™ network security management solution provides centralized management to help operators implement consistent security policies across a hybrid cloud environment.
Federal 5G networks will provide multi-domain access, host sensitive data, and provide control over mission-critical sensors. Using a Zero Trust approach to application security is the best way to ensure the confidentiality, integrity, and availability of the data, applications, assets, and services (DAAS) to accommodate differing levels of user access permissions. A Zero Trust implementation relies on granular access policies, map- ping subscribers and hardware to the DAAS. Palo Alto Networks 5G-native security allows contextual information to be taken from the user plane function and applied to segmentation policies in the MEC, private clouds, or public clouds. Instead of relying on standard segmentation approaches like IP address or username, 5G enables more granular segmentation by defining which subscribers and types of hardware can access applications, using identification methods like IMSI and IMEI.
As federal agencies develop applications to take full advantage of 5G, shifting security into the development process through DevSecOps will go a long way to ensuring application integrity. The right security tools can provide guardrails to enable high-velocity development without any security compromise. Palo Alto Networks Prisma® Cloud Compute Edition integrates with the continuous integration tools developers use to drive automation. This best-in-class host and container security solution provides continuous monitoring of application components throughout the software development lifecycle while offering proactive protection.
Protecting Networks
Attacks on the underlying infrastructure are among the larg- est threats to 5G networks. In early implementations of 5G, such attacks have largely included usage of the network and 5G protocols. The best method to stop this type of outage-causing attack is to inspect the GPRS Tunneling Protocol (both GTP-C and GTP-U) traffic and establish security visibility and control to prevent attacks, threats, and vulnerabilities (e.g., floods of traffic to packet core resources). Using App-ID, our NGFW inspects Stream Control Transmission Protocol (SCTP) traffic to detect and prevent protocol anomalies or known ex-ploits. Beyond protecting against misuse and exploitation of 5G signaling protocols, Palo Alto Networks inspects network traffic and prevents distributed denial-of-service (DDoS) attacks by dropping traffic that is overwhelming traffic patterns. Preventing attacks against the packet core is the best way to ensure availability of 5G transport.
It Takes a Platform
Ultimately, no security solution is completely impervious. Combining multiple capabilities into an integrated platform is required to effectively prevent successful attacks.
Palo Alto Networks delivers a robust security platform that provides end-to-end protection for 5G networks that will soon be running many agency mission-critical operations. Open integration will be key to securing a 5G solution.
Our solution enables information-sharing, allowing for continuous monitoring and proactive, automated security. Our single platform, which integrates with 5G core capabilities, will help agencies ensure stability, performance, availability, and integrity of 5G infrastructure and devices.
For more information, please visit paloaltonetworks.com/ us-federal.
1. “NIST Special Publication 800-207,” National Institute of Standards and Technology, August 2020, https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf.




